Welcome to the “From Zero to Hardware Hacker” series, where I document my foray into the world of hardware hacking. Recently, on the recommendation of my CTF peers, I purchased a Yardstick One. Initially unfamiliar with the specifics, I researched and found that the ANT500 antenna, covering a frequency range of 75 MHz to 1 GHz, is highly recommended for beginners—though I’m still exploring why. As a novice equipped with an affordably priced radio-controlled garage door, I’ve chosen this as my entry point into RF hacking. For security reasons, I will omit certain details like brand names and models. This series will chronicle my journey into a new aspect of cybersecurity: hardware hacking.
Stay tuned for the next installment, where I will delve into the analysis of radio commands used to control my garage door, following the arrival of my SDR device.
Information gathering
In this post, I explore a commonly used garage door opener that comes with two remote controls for remote operation. Despite extensive online searches, details about the remote control proved elusive. Nevertheless, a closer look at other remotes from the same manufacturer, as well as compatible replacement remotes, revealed that they operate at a frequency of 433.92 MHz. This frequency is commonly used and can be verified through spectrum analysis. Moving forward with my experiments, I decided to use rfcat to delve deeper into the device’s communication. To begin, I needed to establish communication between rfcat and my Yardstick device, which required creating a udev rule. This setup is essential for enabling the communication needed for my analysis :
/etc/udev/rules.d/20-rfcat.rules :
# legacy RfCats and cc1111usb
SUBSYSTEMS=="usb" ATTRS{idVendor}=="0451" ATTRS{idProduct}=="4715" MODE:="0660" SYMLINK+="RFCAT%n", GROUP="dialout"
# modern RfCats
SUBSYSTEMS=="usb" ATTRS{idVendor}=="1d50" ATTRS{idProduct}=="6047" MODE:="0660" SYMLINK+="RFCAT%n", GROUP="dialout"
SUBSYSTEMS=="usb" ATTRS{idVendor}=="1d50" ATTRS{idProduct}=="6048" MODE:="0660" SYMLINK+="RFCAT%n", GROUP="dialout"
SUBSYSTEMS=="usb" ATTRS{idVendor}=="1d50" ATTRS{idProduct}=="605b" MODE:="0660" SYMLINK+="RFCAT%n", GROUP="dialout"
# RfCat bootloader subsystem (uses it's own product id)
SUBSYSTEMS=="usb" ATTRS{idVendor}=="1d50" ATTRS{idProduct}=="6049" SYMLINK+="RFCAT_BL_C" ENV{ID_MM_DEVICE_IGNORE}="1"
SUBSYSTEMS=="usb" ATTRS{idVendor}=="1d50" ATTRS{idProduct}=="604a" SYMLINK+="RFCAT_BL_D" ENV{ID_MM_DEVICE_IGNORE}="1"
SUBSYSTEMS=="usb" ATTRS{idVendor}=="1d50" ATTRS{idProduct}=="605c" SYMLINK+="RFCAT_BL_YS1" ENV{ID_MM_DEVICE_IGNORE}="1
Once the Yardstick is configured to interface with your computer, the next step is to install the ‘rfcat’ tool, which is essential for conducting our spectrum analysis. Rfcat provides a powerful and flexible platform for working with radio frequencies, making it an ideal choice for exploring and manipulating RF signals.
# installation of rfcat
git clone https://github.com/atlas0fd00m/rfcat.git
cd rfcat
python -m venv venv/
source ./venv/bin/activate
python setup.py install
# detect dongle and open a shell
./rfcat -r
Once ‘rfcat’ is installed, the final step is to perform the spectrum analysis :
>> d.specan(433920000)
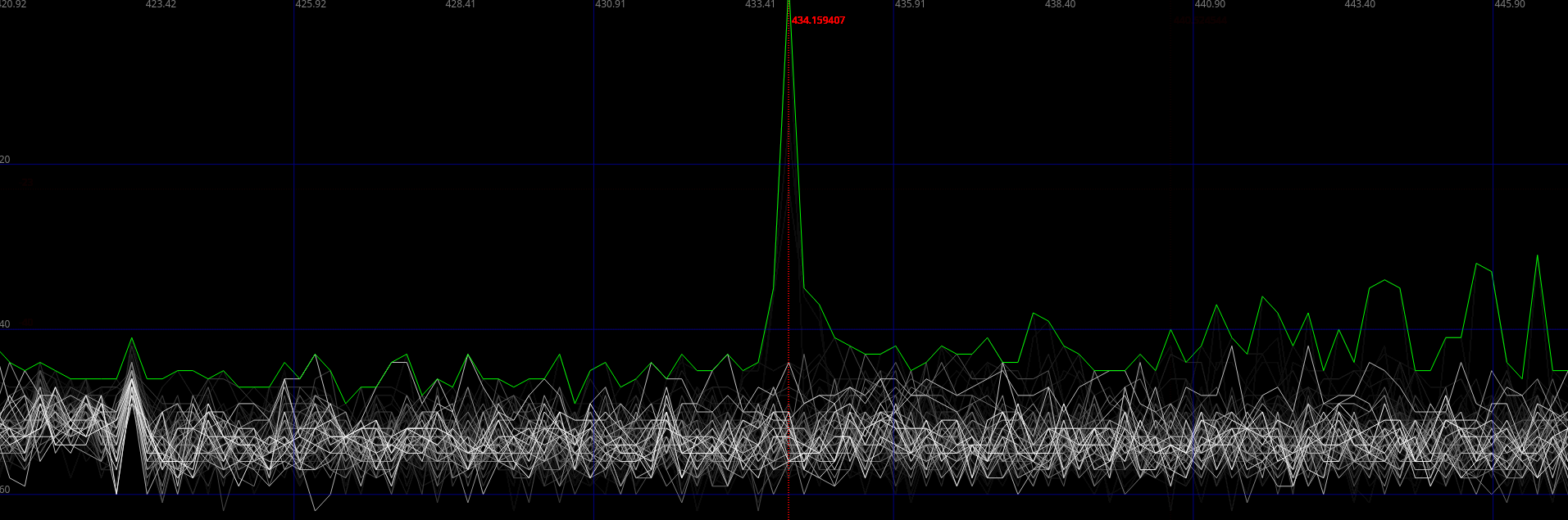
The most common digital modulation schemes you’ll typically encounter in the specifications for devices like garage door openers are Frequency Shift Keying (FSK) and Amplitude Shift Keying (ASK). These modulation techniques are crucial for the transmission of digital data over radio waves. FSK works by varying the frequency of the carrier signal to represent data, while ASK/OOK varies the amplitude of the carrier signal. FSK (Frequency Shift Keying) can be identified by the presence of multiple characteristic peaks, whereas ASK/OOK (Amplitude Shift Keying/On-Off Keying) typically displays only one peak.
Read data
Now that the operating frequency has been confirmed, the next step is to capture the activity on this channel using the Yardstick and RfCat :
d.setFreq(433920000)
d.setMdmModulation(MOD_ASK_OOK)
d.setMaxPower()
d.lowball()
I opted for MOD_ASK_OOK modulation, widely used for devices characterized by a single peak in their spectrum. Despite this logical choice, it proved ineffective. After testing every modulation option available on RfCat with the Yardstick, I still haven’t achieved any results. To accurately identify the correct configuration, it’s clear that a more thorough exploration with classic Software Defined Radio (SDR) tools is required. Unfortunately, my current equipment setup does not support such in-depth analysis.
Conclusion
Indeed, the Yardstick cannot perform SDR functions as it is not designed for this purpose, a detail I overlooked when purchasing the device. It serves well as a basic radio transmitter-receiver. Initially, I chose this device to avoid the cost of more expensive equipment like the HackRF One or the BladeRF, aiming to build my skills in radio hacking before potentially investing in more advanced tools.
The analysis of radio commands used to manipulate my garage door will be further explored in an upcoming article, following the acquisition of a device capable of performing SDR.