Welcome back to “Road to OSCP”, a series where I share my journey toward obtaining the OSCP certification. In this second episode, we turn our attention to the “Blue” machine on the “Hack the Box” platform. Like the previous machine we tackled, “Blue” is based on Windows, providing another opportunity to hone our skills in a familiar yet challenging environment.
Enumeration
First, we’ll conduct an nmap scan to identify what services are running :
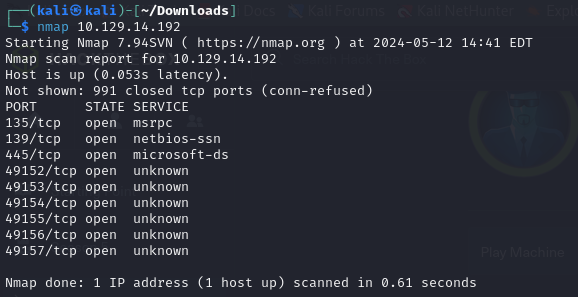
Given the similarities to the “Legacy machine,” it appears we have several ports open on the “Blue” machine, suggesting the likelihood of a SAMBA server running. To obtain more detailed information and confirm our suspicions, we will proceed with a deeper scan :
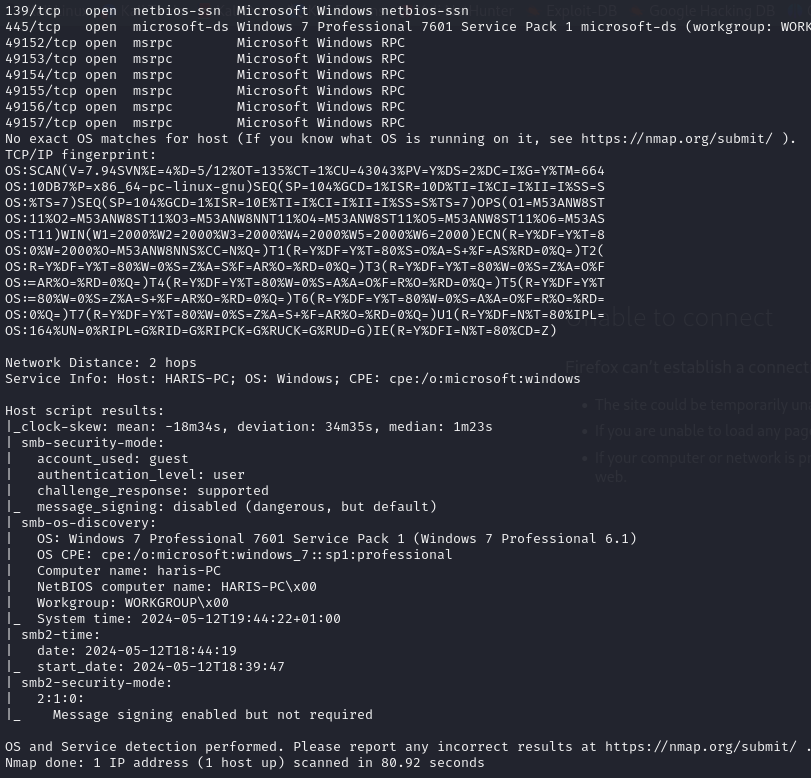
Let’s go ahead and initiate a simple nmap scan. While this method isn’t always definitive, identifying a vulnerability early on can offer a quick and effective advantage.
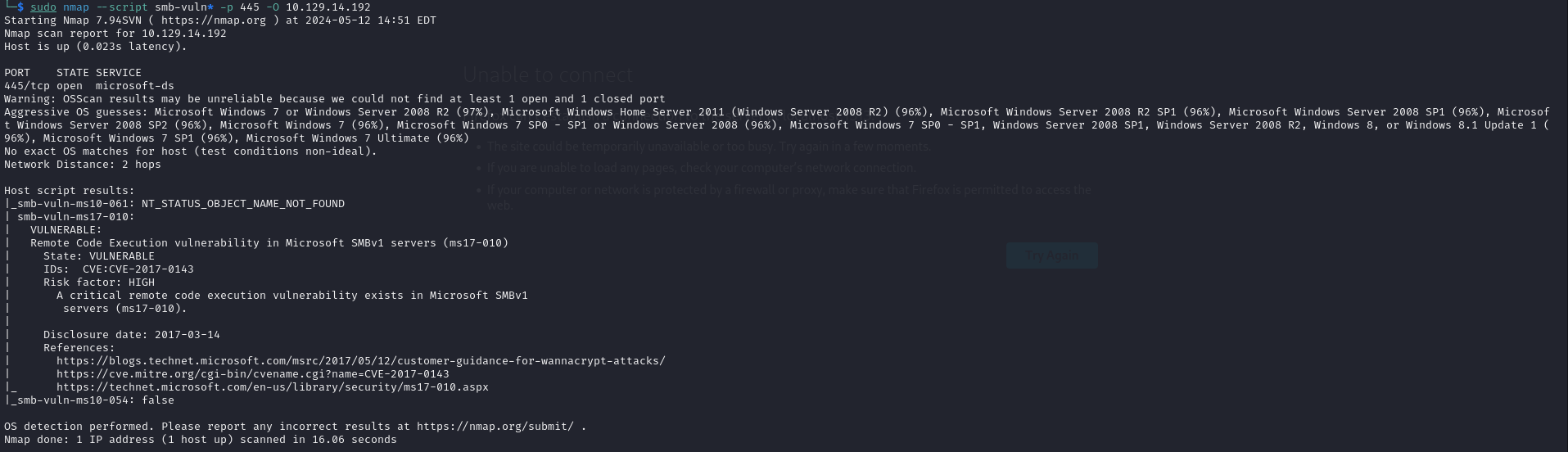
Exploitation
The MS-010 (EternalBlue) exploit can be easily leveraged using Metasploit. This tool is especially useful during time-sensitive exams like the OSCP because it enables rapid exploitation, which is key to efficiently managing the constrained time available.
Note: The target IP has changed due to a system crash.
It’s not necessary to perform privilege escalation as the session already has admin rights.
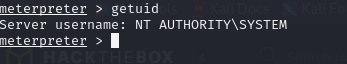
Conclusion
I’m a little disappointed with this machine. As a legacy, there is no Privesc, and the method to win the machine is strictly the same. I hope the next machines will be more challenging.