One of the main goals of purchasing the BladeRF is to delve into GSM hacking, specifically targeting 2G networks (SMS and MMS). This article aims to explore this field, starting with passive reconnaissance as the initial step in our investigation. I am very excited to embark on this journey. However, it is important to note that this activity is legally borderline. I urge you to respect people’s privacy, be mindful of your actions, and avoid intruding into others’ lives.
Scan Base Transceiver Stations (BTS)
The first thing you can do is to list all the nearby Base Transceiver Stations (BTS) using the grgsm_scanner tool. On ArchLinux, the installation can be done via Git with the following command. This tool is available in the AUR repositories for Arch Linux users. For Ubuntu users, grgsm_scanner is part of the official repositories.
yay gr-gsm-git
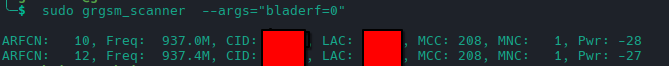
Here are some key terms and explanations:
- ARFCN (Absolute Radio Frequency Channel Number): This is the channel number used.
- Freq: Each channel has a fixed frequency associated with its ARFCN.
- CID (Cell Identifier): This is the identifier of the transmitting cell.
- LAC (Location Area Code): This code identifies a location area within the GSM network.
- MCC (Mobile Country Code): This is the country code. MCC 208 corresponds to France.
- MNC (Mobile Network Code): This is the code of the operator running the cell.
- Pwr: This indicates the power of the received signal.
If you need information about cell towers, their locations, and useful tools, you can use the very practical resource: OpenCellID.
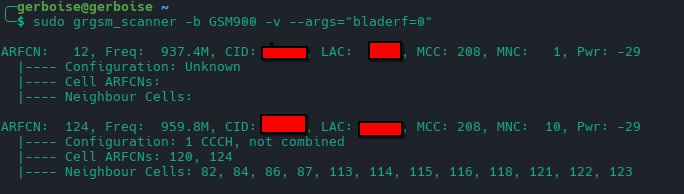
By specifying frequency bands in the scanner command, the tool displays more detailed information. An important detail revealed is the ‘Cell ARFCNs,’ which are the uplink channels used by mobile devices. These channels are displayed when a specific frequency band is included in the command. This added layer of information is crucial for a deeper understanding and more precise analysis of the signals.
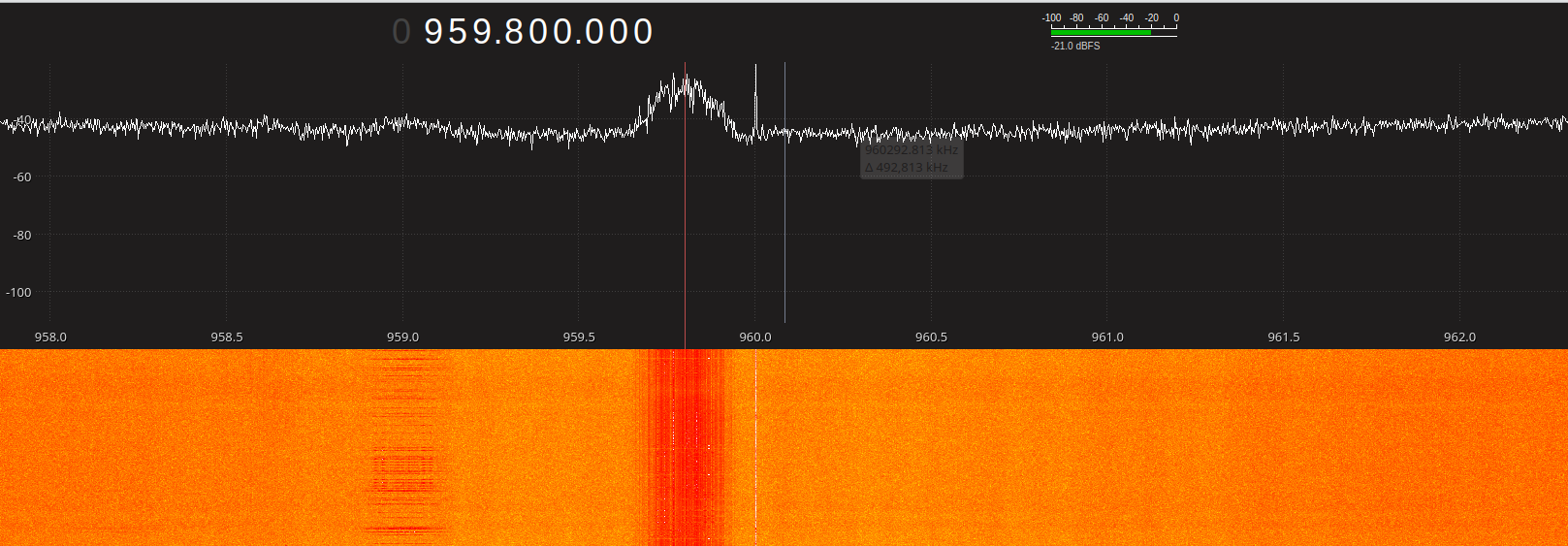
It is possible to observe activity corresponding to ARFCN 124 via GQRX :
Analyze packets live
grgsm_livemon is a graphical tool that enables real-time monitoring of data transmitted on a given frequency. The unique feature of this tool is its ability to interface with Wireshark through a loopback by wrapping GSM packets in UDP to create a packet called GSMTA. Contrary to what is stated in most documentation found online, nothing is captured on my system unless the option –collectorport 4729 is specified.
Thus, we can open Wireshark with the following command: sudo wireshark -k -f udp -Y gsmtap -i lo &. This command starts the capture of UDP packets only (-f udp), filtering for GSMTAP requests (-Y gsmtap) on the loopback interface (-i lo). The -k option ensures the capture begins immediately upon launching. It’s important to properly adjust the gain and frequency corresponding to the ARFCN in the grgsm_livemon GUI to capture the signal effectively.
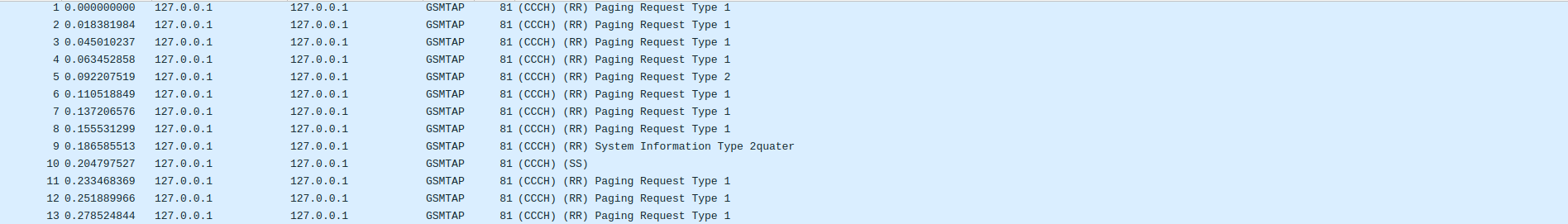
We will see in a following chapter how to use this type of capture to decode transmissions.
Cature GSM network activity
Another great tool in the grgsm suite is grgsm_capture. This tool allows capturing GSM traffic and saving it to a file. Unlike Wireshark captures, which do not allow direct decoding of SMS and calls, this type of capture can be analyzed and decoded.
sudo grgsm_capture -f 959.8e6 capture_9598.cfile --args="bladerf=0"
Captured packets can be saved to a file for analysis, similar to using LiveCapture in Wireshark. This is achieved by wrapping GSM frames in UDP packets and sending them through the loopback interface. The grgsm_decode command takes two parameters: -c <FILE> and -a <ARFCN>.
grgsm_decode -c ./capture_9598.cfile -a 124
Decoding SMS
In GSM, there are channels with different purposes. The channel of interest in this article is the SDCCH8 channel, which is used for:
- Call setup and release.
- Location updating (registering the mobile phone on the network as it moves).
- Sending and receiving SMS.
- Authentication and encryption key management.
The SDCCH is a dedicated logical control channel in the GSM network. It is a type of channel used for signaling and low-rate communications between the mobile and the base station. The SDCCH8 refers to a specific configuration where a physical time slot is divided into 8 logical SDCCH sub-channels used for multiplexing. To decode this type of frame, use the following command:
grgsm_decode -c ./capture_9598.cfile -a 124 -m SDCCH8
Note that much of the documentation filters with timeslot. However, it is possible to do this directly in Wireshark with the following filter: gsmtap.ts == 6.
gsm_a.dtap.msg_rr_type == 0x3f
gsm_a.rr.SC == 1